Create Azure credentials for use in GitHub Actions
Join me in this blog post as I look at how you can create an Azure Service Principal to make a connection between your Azure subscription and GitHub Actions.

One of the things you can do with GitHub Actions is to connect with your Azure subscription. You can interact with your Azure resources, deploy Azure resources, and more.
In order to be able to use GitHub Actions with your Azure subscription, you need to create that service connection. To do that, you must create an Azure Service Principal and store the credentials inside a GitHub Actions secret.
Create the Service Principal
Creating a Service Principal is the first step to creating that connection between GitHub Actions and Azure. You can do that in a few ways:
The quickest way and easiest way I've found to create this Service Principal is to use Azure CloudShell and issue the command:
New-AzADServicePrincipal -DisplayName "GitHubActionsConnection"
Now we have the Service Principal created, we need to create a secret/password that can be used to log in with. For this, we need to head to the Azure Portal. Go to:
Azure Portal > Microsoft Entra ID > App Registrations
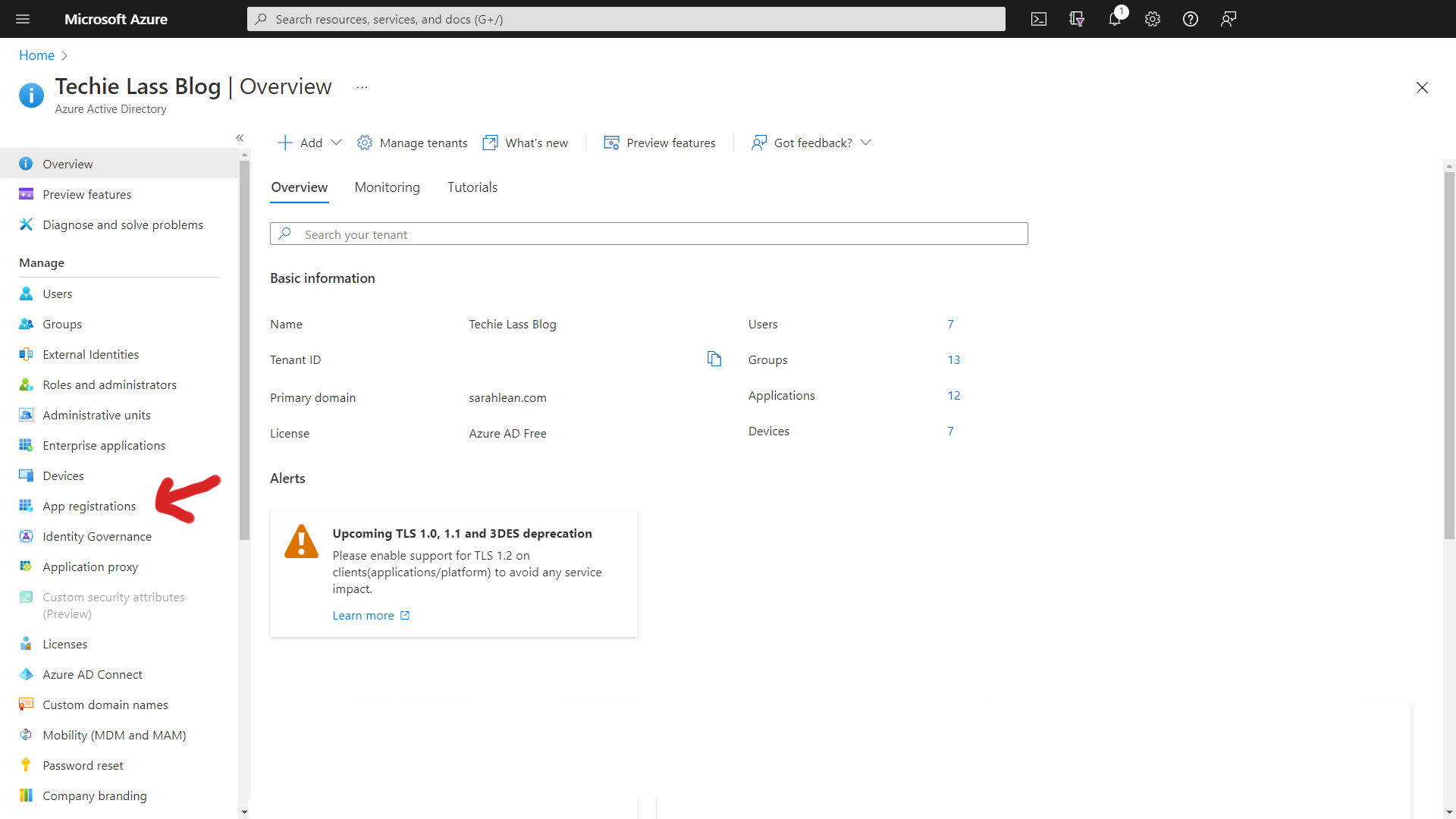
Click on "All Applications" and click on your newly created Service Principal.
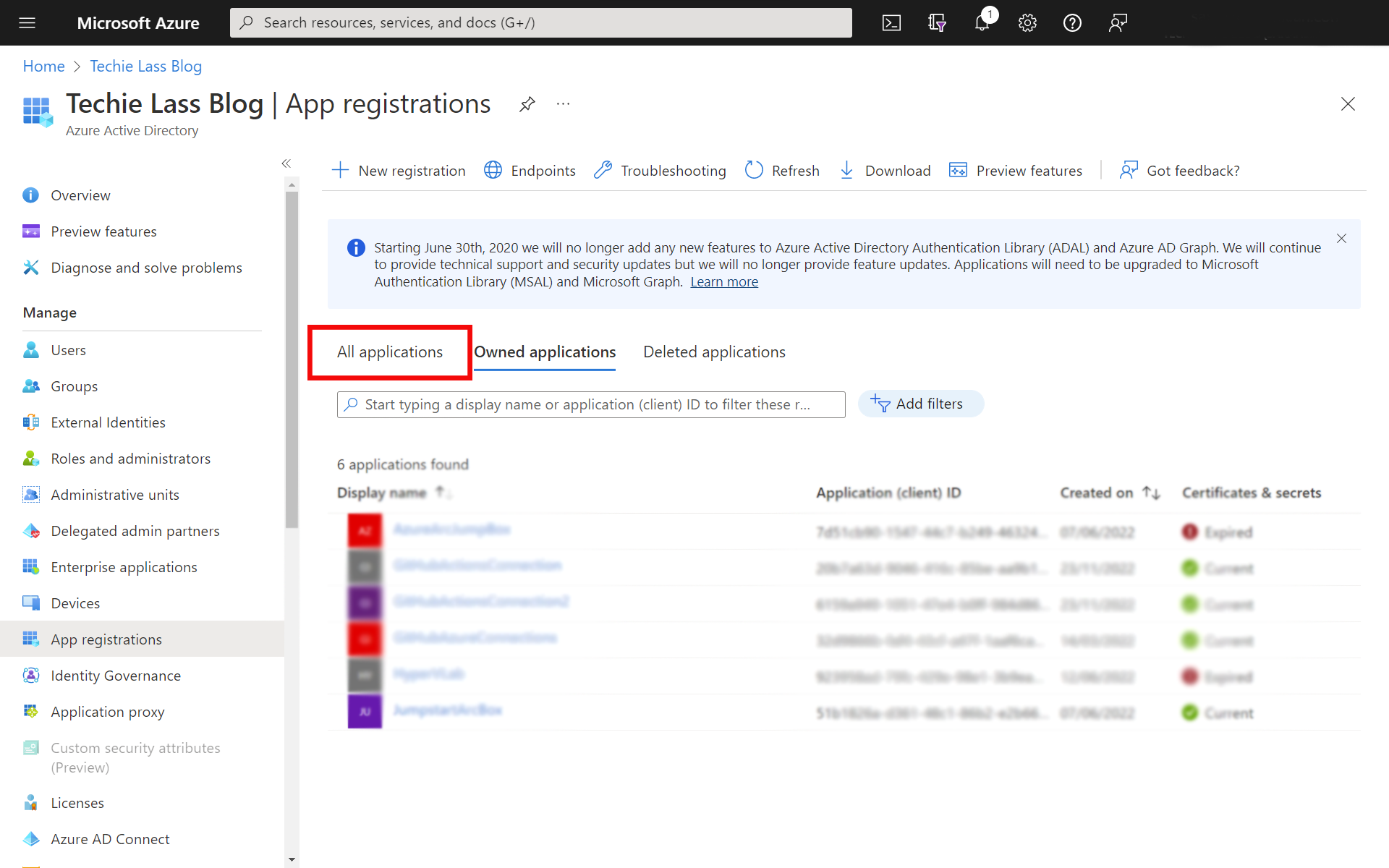
Now click on "Certificates & Secrets" and click on "New Client Secret".
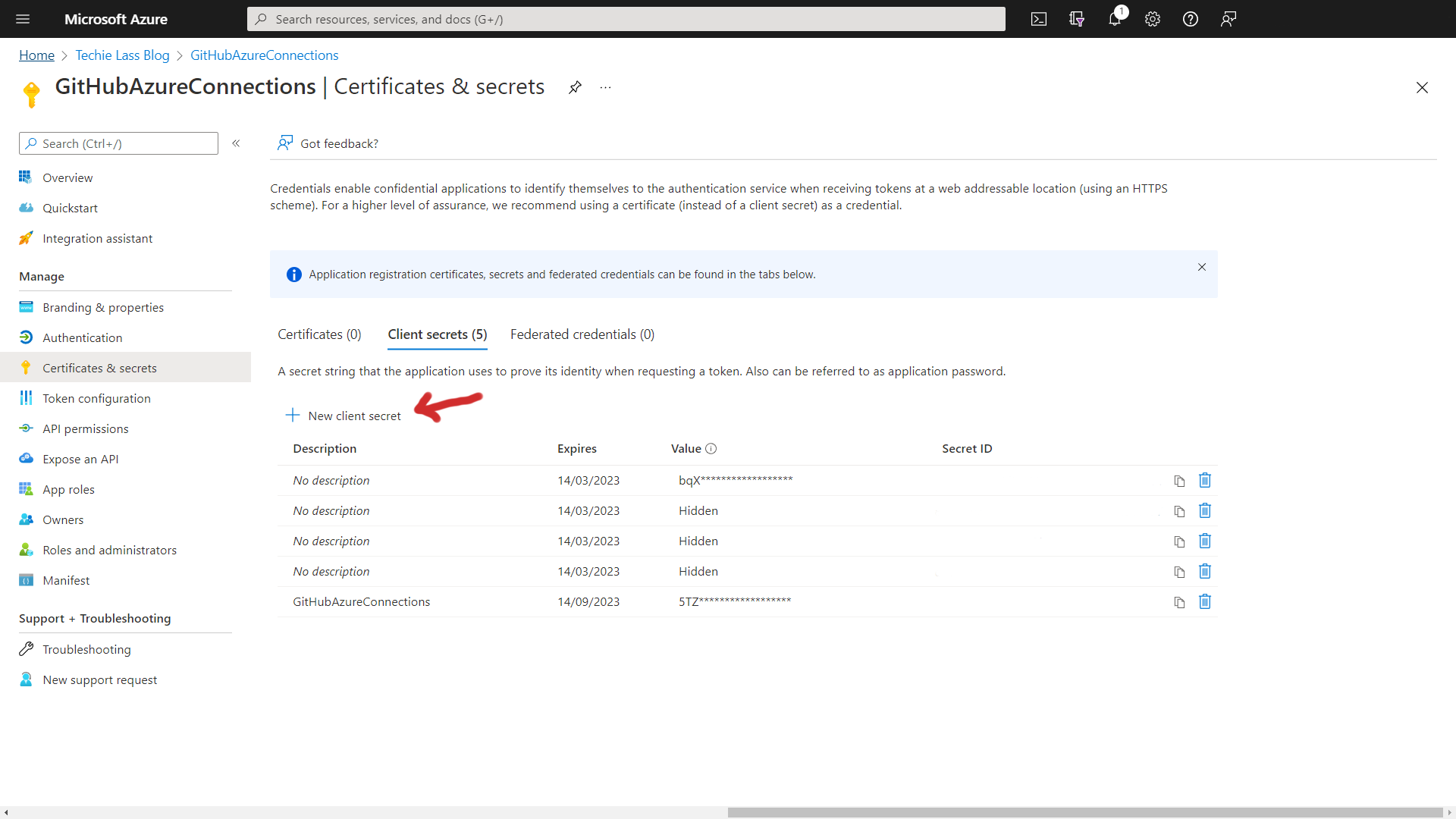
You get the option to set how long this secret will be available, please use your organisation's best practices here.
Permissions
We now need to give this Service Principal rights to either a resource group or subscription. In this example, I am going to set up permissions for this Service Principal over my subscription.
To do that, I go into the Azure Portal > Subscriptions and select the subscription.
Now I click on Access Control (IAM) down the left-hand side.
Then clicking on Add to create a new role assignment.
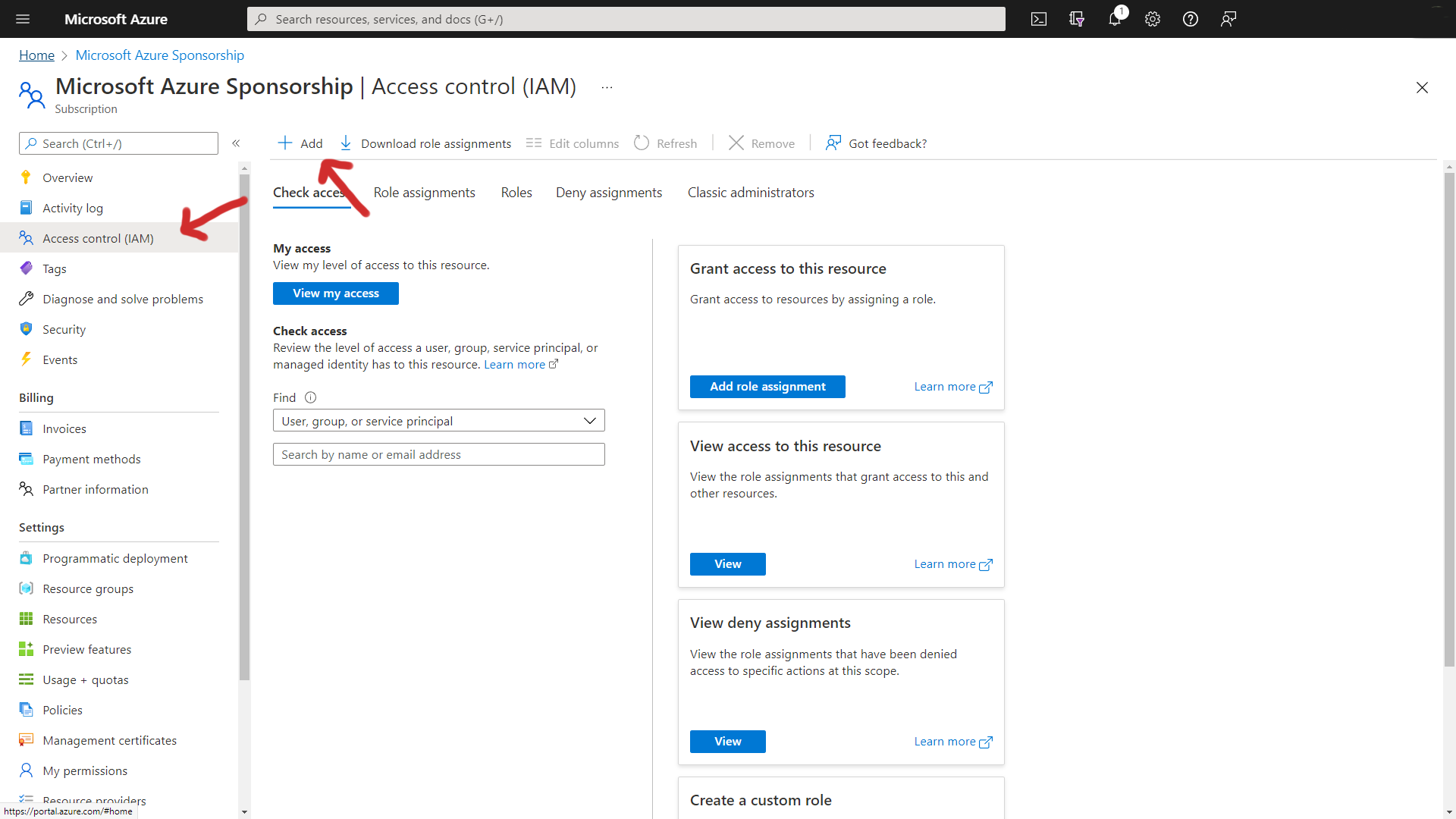
You'll have the option of assigning a number of permissions to the Service Principal. I will assign Contributor permissions here and then select the new Service Principal as a member.
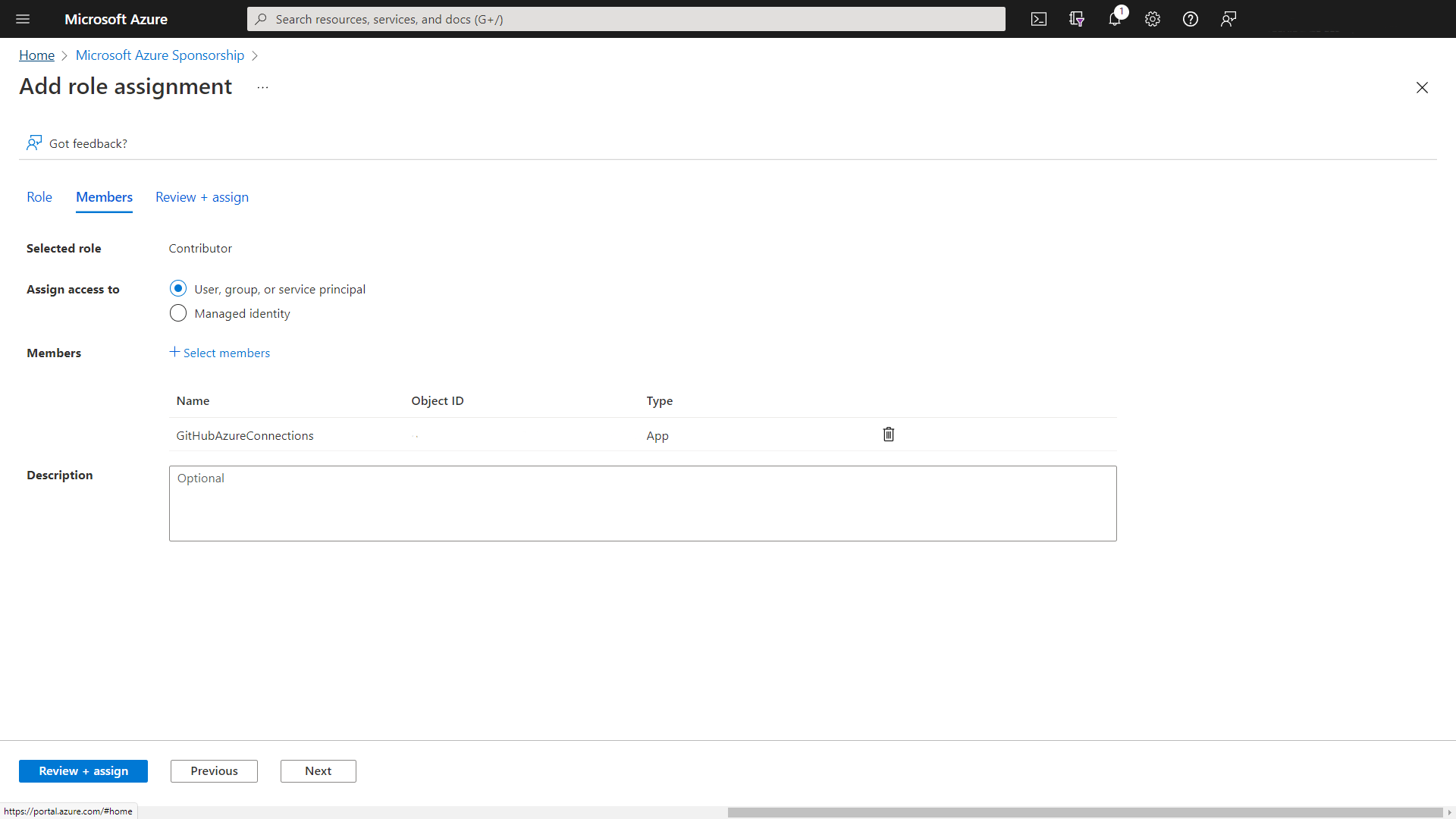
Once the permissions have been applied, it's time to collect all the information to store it inside GitHub for use within the workflows.
Collect Service Principal information
To store the information inside a GitHub Actions secret, it needs to be stored within a JSON format. We can run this PowerShell subscription to collect all the information you will need for GitHub and in the form that GitHub needs.
# Fill in the information information with the Service Principal Name you created and your Azure Subscription Name.
$ServicePrincipalName = "GitHubActionsConnection"
$AzSubscriptionName = "Name_of_your_subscription"
Connect-AzureAD
$Subscription = (Get-AzSubscription -SubscriptionName $AzSubscriptionName)
$ServicePrincipal = Get-AzADServicePrincipal -DisplayName $ServicePrincipalName
$AzureADApplication = Get-AzureADApplication -SearchString $ServicePrincipalName
$OutputObject = [PSCustomObject]@{
clientId = $ServicePrincipal.AppId
clientSecret = (New-AzureADApplicationPasswordCredential -ObjectId $AzureADApplication.ObjectId).Value
subscriptionId = $Subscription.Id
tenantId = $Subscription.TenantId
}
$OutputObject | ConvertTo-Json
Store Azure Credentials in GitHub Secrets
Take a copy of the output from the PowerShell query. This will be stored inside a GitHub Secret for use within your workflows.
Within the repository where your workflow is, click on Settings > Secrets > Actions and then click on new repository secret.
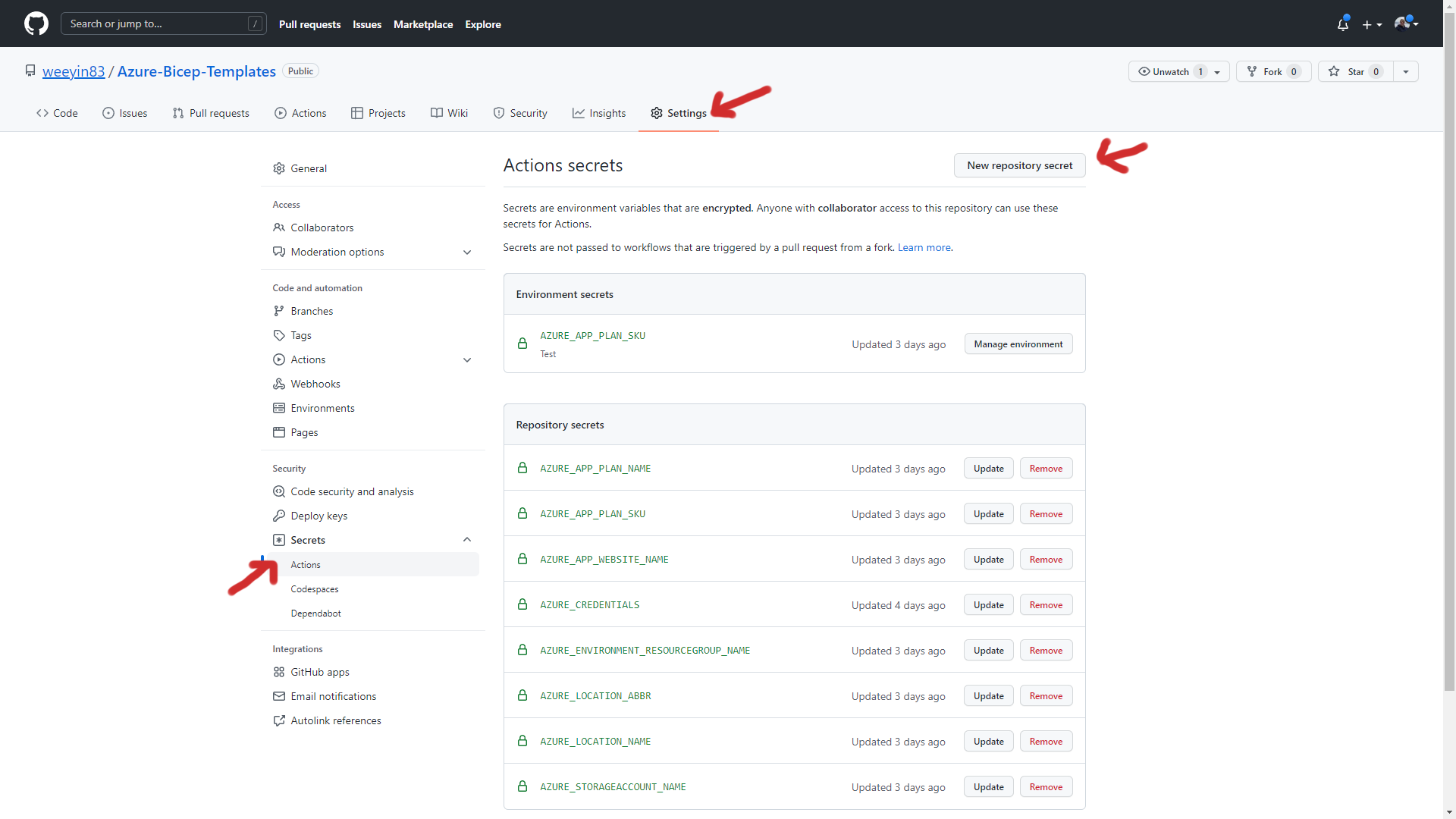
Give the new secret a name; I usually go with "Azure_Credentials" and then paste the PowerShell script's output into the value section.
Use the Azure login action
Now you have the Service Principal set up and the information stored inside GitHub Secrets, it's time to use that information.
You can use the Azure Login action within your workflow and call that secret information.
You can continue to build on the workflow from there. 👍
on: [push]
name: AzureLogin
jobs:
build-and-deploy:
runs-on: windows-latest
steps:
- name: Log in with Azure
uses: azure/login@v1
with:
creds: '${{ secrets.AZURE_CREDENTIALS }}'