What is Terrascan?
Exploring Terrascan and how it can be used to improve your Infrastructure as Code security and compliance standards.

Let's dive into a tool that's making waves in the realm of cloud infrastructure security – Terrascan. If you've been exploring the vast landscape of Infrastructure as Code (IaC), you might have stumbled upon this powerful tool. But fear not if you haven't! I'm here to guide you through what Terrascan is all about and why it's becoming a must-have in the toolkit of cloud engineers.
What is Terrascan used for?
Terrascan is a static code analysis tool specifically designed for IaC. In simple terms, it helps ensure that the code used to provision and manage cloud infrastructure adheres to best practices, compliance standards, and security policies. Whether you're using Terraform, Kubernetes YAML, Helm charts, or other IaC tools.
Terrascan features
Now, let's take a closer look at what makes Terrascan shine:
1. Comprehensive Policy Checks: Terrascan comes packed with a wide array of built-in policies covering security, compliance, and operational best practices. It can identify misconfigurations, security loopholes, and potential pitfalls in your infrastructure code.
2. Multi-Cloud Support: Whether you're deploying on AWS, Azure, Google Cloud, or any other major cloud provider, Terrascan supports them all. This flexibility makes it a go-to choice for organizations with multi-cloud environments.
3. Custom Policy Definition: While the built-in policies cover many common scenarios, Terrascan also allows you to define custom policies tailored to your organization's specific requirements. This feature empowers teams to enforce internal standards and policies seamlessly.
4. Integration with CI/CD Pipelines: Terrascan seamlessly integrates into CI/CD pipelines, enabling automated scanning of infrastructure code during the development and deployment process. This helps catch issues early in the development lifecycle, reducing risk and ensuring compliance.
How to install Terrascan on Windows
Here's a quick guide to help you install Terrascan on Windows:
Install Chocolatey (if not already installed)
Chocolatey is a package manager for Windows that simplifies the process of installing software.
If you haven't already installed Chocolatey, you can do so by opening PowerShell as an administrator and running the following command.
Set-ExecutionPolicy Bypass -Scope Process -Force; [System.Net.ServicePointManager]::SecurityProtocol = [System.Net.ServicePointManager]::SecurityProtocol -bor 3072; iex ((New-Object System.Net.WebClient).DownloadString('https://chocolatey.org/install.ps1'))
Install Terrascan using Chocolatey
Once Chocolatey is installed, you can use it to install Terrascan by running the following command in PowerShell as an administrator:
choco install terrascan
This command will download and install Terrascan along with its dependencies.
Verify Terrascan installation
To ensure Terrascan has been installed correctly, you can verify its installation by running the following command in PowerShell:
terrascan --version
If Terrascan has been installed successfully, you should see the version number displayed in the output.
And there you have it! Terrascan is now ready to help you secure your infrastructure code on Windows.
How to use Terrascan to scan the IaC code
Using Terrascan to scan your IaC code is a straightforward process. Here's a basic overview:
Navigate to Your IaC Directory: Open a command prompt and navigate to the directory containing your Terraform, Kubernetes YAML, or Helm chart files.
Run Terrascan: Simply execute the `terrascan scan` command. Terrascan will analyze your IaC files against its predefined policies and provide a detailed report of any violations found.
Review the Results: Once the scan is complete, review the generated report to identify any issues or potential risks in your infrastructure code.
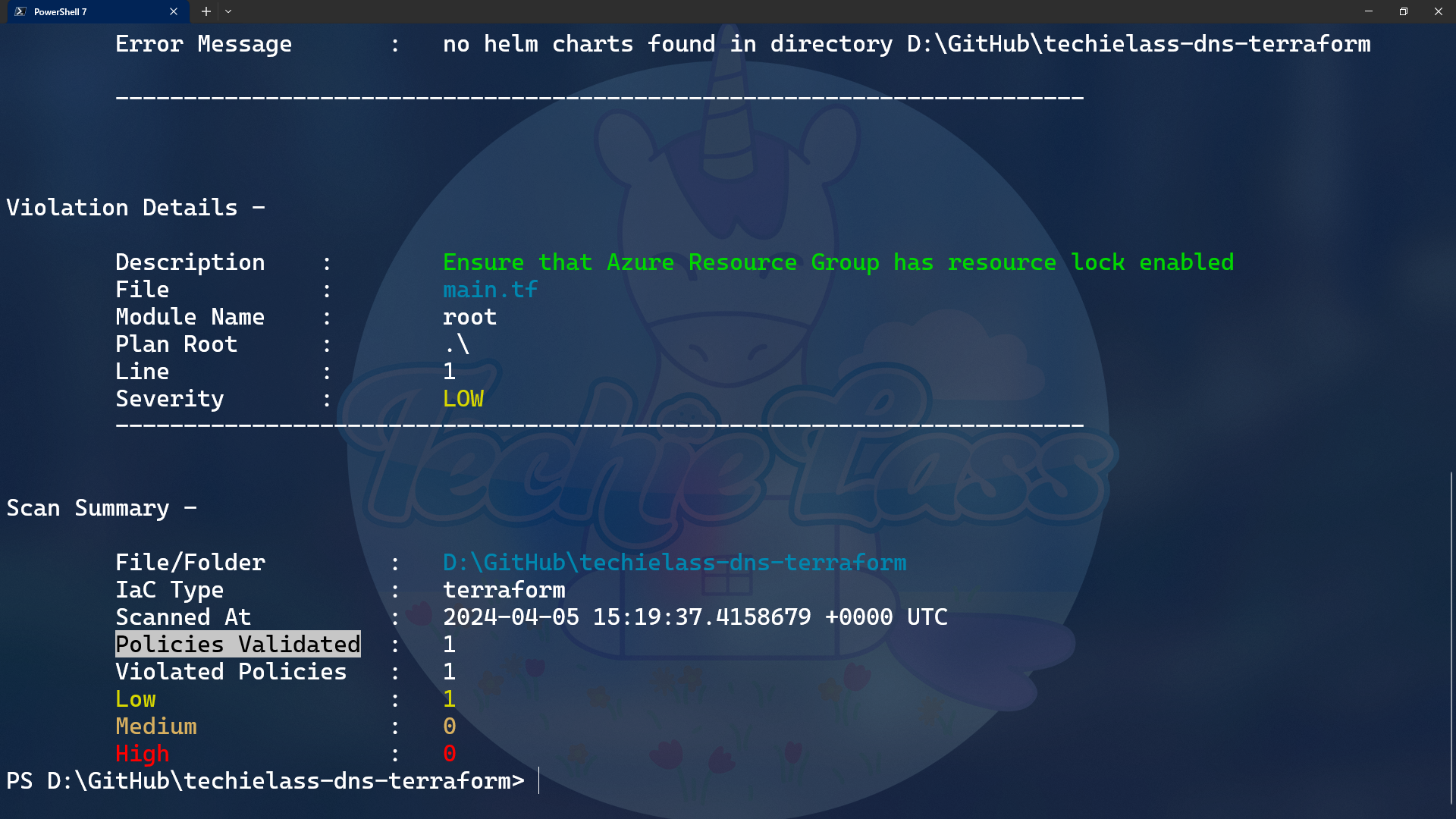
Take Action: Address any identified issues by making necessary adjustments to your IaC code, and rerun the scan to ensure compliance.
Terrascan custom policies
One of the standout features of Terrascan is its support for custom policies. Here's how you can define and use custom policies with Terrascan:
- Policy Definition: Write your custom policies using the Rego language, following the Terrascan policy framework.
- Policy Configuration: Configure Terrascan to load your custom policies alongside the built-in ones during scans.
- Scan with Custom Policies: Run Terrascan as usual, and it will evaluate your infrastructure code against both built-in and custom policies.
Custom policies empower organizations to enforce specific security and compliance requirements tailored to their unique needs, providing an extra layer of assurance when deploying cloud infrastructure.
Conclusion
In a world where security and compliance are paramount, tools like Terrascan are invaluable assets for cloud engineers and DevOps teams. By integrating static code analysis into the infrastructure development lifecycle, Terrascan helps identify and mitigate risks early on, ensuring that your cloud deployments are secure, compliant, and resilient.
So, whether you're a seasoned cloud architect or just dipping your toes into the world of Infrastructure as Code, give Terrascan a try, and experience the peace of mind that comes with knowing your infrastructure code is in good hands. Happy scanning!